
Proactively Protecting Your Sensitive Information for Remote Workers
The unprecedented COVID-19 pandemic has, almost overnight, forced many organizations to modify their business practices and transition to a remote workforce. Of course, the first focus during this transition is deploying the connectivity and infrastructure necessary to support your remote workers. Don’t, however, lose sight of the fact that information scattered across a dispersed workforce can significantly raise the risk of a data breach or other security concerns.
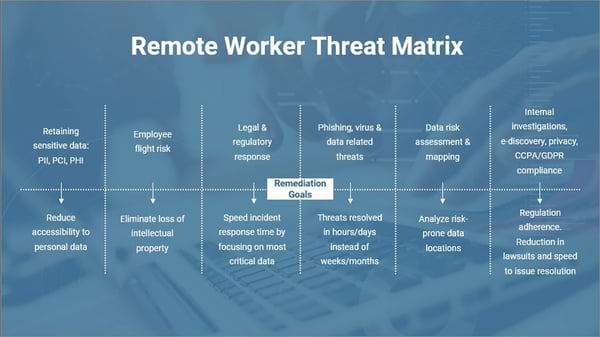
At Gimmal, we regularly talk to IT, security, and privacy professionals across a broad portfolio of industries. As a result of those discussions, we’ve created the threat matrix shown below which outlines the areas of concern that we hear most often:
As a result of content being more decentralized, it is perhaps more important than ever to ensure that your company’s sensitive and critical business information is secure even though your workforce is operating remotely. The goal is to achieve full visibility into any Windows workstation that has an Internet connection. By silently using Microsoft SCCM – or a similar tool – your administrators can manage content being stored on each workstation.
Four Tips to Limit the Risk of Insider Threats:
- Creating specific folder hierarchies on each device. This strategy can help keep project files organized among team members and aid in the disposition of documents once a project has been completed.
- Discovering content on an employee’s workstation by examining meta-data criteria such as file name, type, or age. Users can also open files and search through their content to uncover items containing specific information such as keywords, phrases, or patterns (e.g., social security numbers, customer information, etc.).
- Applying retention rules (i.e., move/delete) to locally stored content based on established records retention guidelines. Additionally, users can facilitate a data owner remediation approach where targeted content is identified automatically then presented to the data owner on a report where they can review each item and indicate the proper disposition step for each item.
- Locating and managing email content that may reside in local PST files on the device, even when the PST file is open in Microsoft Outlook.
More Tips to Gain Control Over Your Remote Workstation Content
The recommendations covered in this post will help you protect your sensitive information while empowering your remote workforce.
For more best practices to ensure your information is safe, secure, and accessible, download a free copy of this ebook.
We worked with the industry's elite to develop this resource covering the best practices and tips for creating, capturing, collaborating, and rising to new levels of content management excellence. Click through below to preview what's included and then download your copy here.
About Gimmal
Without proper management of your information, you could be exposing your organization to legal or regulatory risks. Gimmal helps you take control of your information by streamlining the discovery, migration, governance, and compliance of information without impacting your end users. Achieve information governance by ensuring information creates value instead of risks. For more information visit www.gimmal.com.


